
The proliferation of smart gadgets has revolutionized the way we interact and stay with technology. From smart home equipment to wearable devices and commercial automation, the adaptability of IoT (Internet of Things) has continued to spread around the world. However, with these advancements comes the risk of cybersecurity threats. In this blog, we will discover the risks associated with IoT gadgets and provide sensible hints to safeguard your smart devices from cyber threats.
Top IoT threats
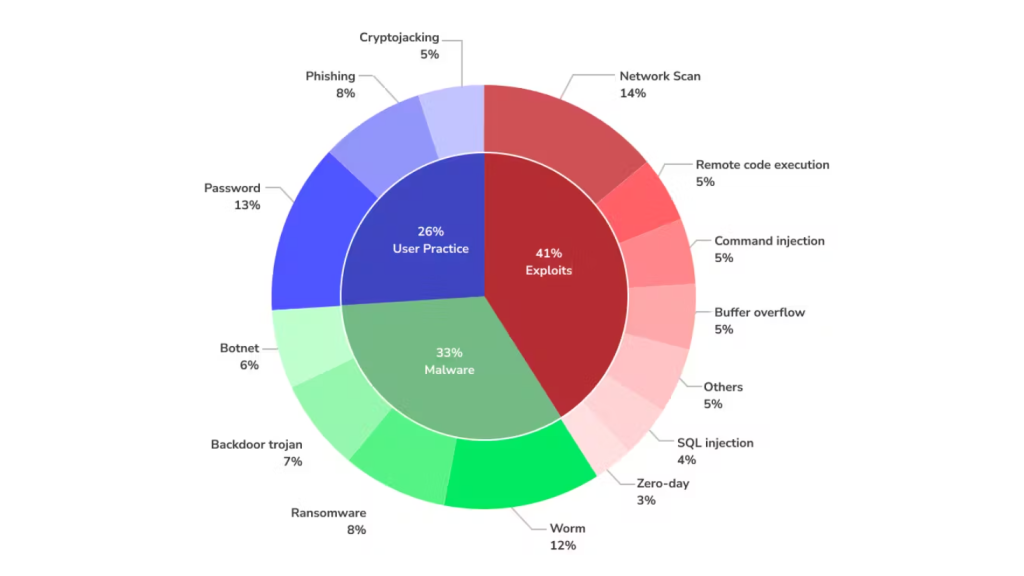
- Device Vulnerabilities: Smart devices, frequently designed with convenience in thoughts, may additionally prioritize functionality over protection. Outdated firmware, susceptible passwords, and unencrypted communication channels are commonplace vulnerabilities that attackers may prey on.
- DDoS Attacks: IoT botnets may be harnessed to launch big Distributed Denial of Service (DDoS) assaults, overwhelming servers and causing downtime for crucial services.
- Data Breaches: Connected gadgets acquire great quantities of personal records, making them an attractive target for hackers intending to gain access to sensitive data for identification theft or extortion.
- Malware and Ransomware: Cybercriminals can use malware to gain unauthorized access to your smart gadgets or lock you out thru ransomware and claim some payment so that they can restore access to services.
So How Can You Protect your smart devices?
- Secure Network: Ensure your private home Wi-Fi network is encrypted with WPA2 or better encryption. Change the default username and password of your router and regularly replace the firmware to patch any vulnerabilities.
- Strong Passwords: Use particular, strong passwords for every IoT device. Avoid using default credentials and don’t forget the usage of password managers to address a couple of password securities. Remember not to use password managers which are available on browsers but instead invest in a secure password manager.
- Regular Updates: Keep your smart devices up to date with modern firmware and security patches. Manufacturers often release updates to deal with recognized vulnerabilities. This keeps them secure from the latest attacks.
- Two-Factor Authentication (2FA): Enable 2FA each time viable, because it adds an extra layer of security using requiring a secondary code or authentication approach. A 2FA authentication is a security mechanism that requires two separate and distinct ways of authentication to give access to something.
- Segment Your Network: Consider growing separate networks for IoT devices and essential personal gadgets like computers and smartphones. This limits the impact of potential breaches.
- Disable Unused Features: Turn off any needless capabilities or services on your clever gadgets. Every active provider represents an ability point of access for hackers.
- Using a secure IoT platform: A secure well-rounded IoT platform will help you display all your devices in one platform. This will permit you to maintain an eye on the activities of your devices, push updates regularly, and ensure that all records transmitted to and from the devices are secured and that none of the gadgets are tampered with.
- IoT Security Solutions: Invest in IoT security solutions, together with firewalls and intrusion detection structures, mainly designed to guard linked devices.
- Privacy Settings: Review and regulate privacy settings on your gadgets to limit information collection and sharing to the minimum required.
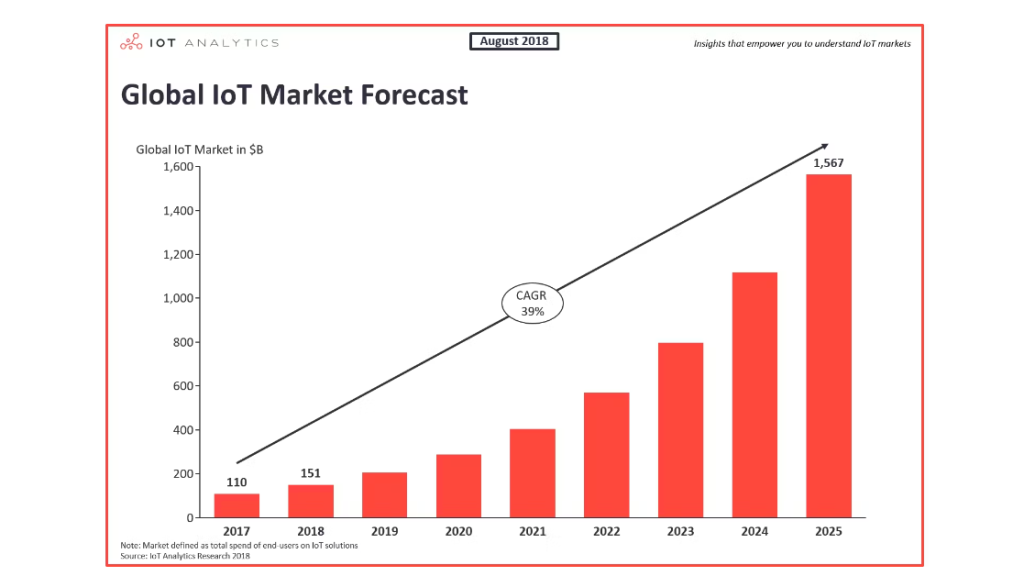
The future of IoT guarantees extra interconnected gadgets, from smart cities to industrial automation. From an analysis done by IOT ANALYTICS, the global market for the Internet of Things (end-user spending on IoT solutions) is expected to grow 37% from 2017 to $151B. It is predicted that the total market will reach $1,567B by 2025.
With this growth comes an elevated necessity for strong cybersecurity measures. Some possible future solutions encompass:-
- Blockchain Technology: Utilizing blockchain can enhance the safety of IoT by using ensuring facts integrity and enhancing authentication.
- AI-driven Security: Artificial Intelligence can assist in predicting and identifying capability cyber threats, providing actual-time responses to assaults.
- Government Regulations: Stricter regulations on IoT security can motivate producers to prioritize the cybersecurity of their merchandise.
Conclusion
As we continue to enjoy and embrace the convenience and innovation of IoT devices, it is important to stay vigilant about the potential cybersecurity threats they pose. By adopting the first-rate practices referred to in this text, you could shield your smart gadgets and personal records from becoming victims of cyber attacks. Stay informed, live stable, and embody the IoT revolution responsibly.











